Diversity
An important system principle not being considered as DoD continues to secure its Maginot Line around the DISN!!
A New Leaf
It has been almost a year since I posted my last blog entry so I decided that it is time. Many have told me that past blog posts have been too long to wade through given our busy lives. I agree and plan to make this and future posts quick reads. I hope to cover a set of topics related to our DoD and Navy information infrastructure and the bureaucracy that helps determine our fielded capability.
The Challenge of Information Assurance
I was recently honored to be a speaker at the Charleston Defense Contractors Association’s C5ISR Conference. It was a great time to catch up with our C2ISR community and to learn from the impressive set of speakers that attended this Charleston SC event. Particularly relevant to our current DoD challenges was the talk given by Ed Amoroso, the AT&T Chief Security Officer. His new book, Cyber Attacks: Protecting National Infrastructure, is available for purchase this month.  In this book he discusses ten principles for improving our Nation’s cyber attack resilience based upon his CSO experience at AT&T. Because our DoD information infrastructure is a subset of our National infrastructure, I highly recommend this book and Ed’s ideas to all of us working National Security. Ed’s recommended principals are:
In this book he discusses ten principles for improving our Nation’s cyber attack resilience based upon his CSO experience at AT&T. Because our DoD information infrastructure is a subset of our National infrastructure, I highly recommend this book and Ed’s ideas to all of us working National Security. Ed’s recommended principals are:
- Tricking Endpoints Using Deception
- Separating Assets Through Design
- Strength Through Diversity
- Balancing Layers of Defense
- Correlating Data to Action
- Collecting and Using Data Intelligently
- Being Situationally Aware
- Providing Dependable Response
- Employing Proper Discretion
- Using Commonality to Highlight Changes
Focusing on Diversity
The Comprehensive National Cybersecurity Initiative (CNCI) has fortunately raised the bar on our collective awareness of information security challenges. Since the stand up of CNCI, the DoD has created the U.S. Cyber Command, U.S. Army Cyber Command, U.S. Air Force Cyber Command, and the U.S. Fleet Cyber Command/10th Fleet, all helping to support this National concern. In my opinion, these National and DoD initiatives were long overdue.
The U.S. Cyber Command and Military Service Cyber Commands are operational commands that support the Joint Combatant Commanders. At the same time, they necessarily carry out their missions upon the information infrastructure supporting the combatant commanders. Within that context and the wisdom contained within Ed’s ten principles, the principle of diversity, as it could be applied to DoD’s network infrastructure, is of particular interest to me.
The Defense Information System Network (DISN) has become the central global infrastructure upon which our Military forces and the associated supporting organizations operate. While it is true that the DISN, which has grown up over the past 20 years, has been built to be resilient through alternate paths with physical diversity between paths, the DISN operates as a DoD protected physical infrastructure that includes both wired and SATCOM transport capability. Within the DISN, the unclassified but sensitive Non-classified Internet Protocol Router Network (NIPRnet), and the classified Secret Internet Protocol Router Network (SIPRnet) operate as the primary networks for DoD operations. What this means is that any DoD information being moved by the DISN can only be protected to the extent that the DISN physical and electronic components can be protected. By consolidating primary communications onto the DISN infrastructure, DoD has effectively challenged potential adversaries to disrupt or spoof this critical resource. This situation is reminiscent of the French Maginot Line of Defense that failed against Germany’s modern blitzkrieg warfare in 1940.
Emerging Alternatives
When the DISN first took shape twenty years ago, our planet had not yet been revolutionized by the power of information and a global Internet to move it. At that time the notion of a global supply chain, outsourced manufacturing, and just-in-time delivery had not been invented. Today the infrastructure supporting this global inter-dependence has grown up to a point where the U.S. is no longer the leading nation in the use of information infrastructure. According to the National Academies of Science report, Rising Above the Gathering Storm, Revisited: Rapidly Approaching Category 5, “The United States now ranks 22nd among the world’s nations in the density of broadband Internet penetration and 72nd in the density of mobile telephony subscriptions.” At the same time, Google has created an information infrastructure that operates in about 46 nations plus the United States, operating an estimated 1 million plus servers. Microsoft and Amazon also operate large computing infrastructures with server numbers estimated to be 40-60% the size of Google. It is difficult to get accurate numbers for these cloud service providers because Google, Microsoft, Amazon, and many other information service provider companies hide such data as proprietary.
It is this growth of global information infrastructure that provides opportunities for the DoD to diversify beyond the DISN infrastructure while at the same time potentially improving the network reach, and performance.  By that I am suggesting that the DoD, and particularly the Navy, should consider connecting into this rich global information infrastructure to support military operations while also diversifying network communications into the global infrastructure.
By that I am suggesting that the DoD, and particularly the Navy, should consider connecting into this rich global information infrastructure to support military operations while also diversifying network communications into the global infrastructure.
Navy: A Unique Opportunity
One aspect of Naval operations, not often considered in the Navy’s information infrastructure, is that other than during open ocean transits, most Naval operations are not far from a shoreline someplace on the planet. If one combines that realization with the fact that the global information infrastructure is large and growing, it is possible to imagine the Navy connected from ship-to-shore-based Internet service providers across the globe. Just as Navy contracts with food and fuel providers in each operating area, it could also contract for ISP services wherever it operates.
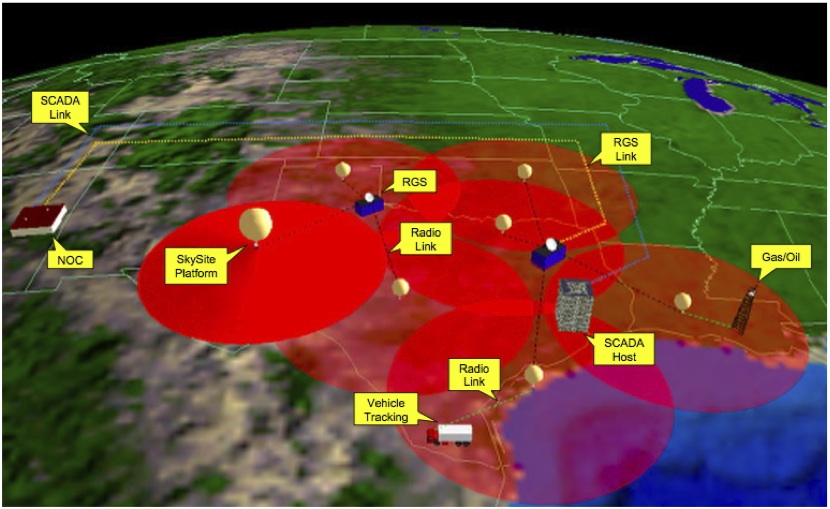
Connecting from ship to these global ISP’s would be a matter of using airborne balloon, unmanned air systems, or manned aircraft to provide ISP compatible over-the-horizon data links. New adaptive antenna technology provides an opportunity for Navy to close the ship-to-shore ISP links using wifi, 3G or 4G technologies at distances that could exceed 100 miles. The Space Data Corporation has provided similar capability to oil companies, the U.S. Air Force, and the Department of Homeland Security using its balloon launched near-space communication packages (http://www.spacedata.net/military.html) since 2004.
The obvious value of such a Navy capability would be significantly increased ship-to-shore bandwidth operating through the diversity of the global Internet infrastructure. Just as the Navy has pioneered defense-in-depth in air defense capability, it may be up to Navy to pioneer DoD network defense-in-depth using such a global ISP concept.


Great article, the principles articulated in the AT&T Chief Security Officer book are thought provoking: need to get the book!
The idea of improving access diversity by access to communication network fabric below the satellite layer is a good idea that never seems to get traction. During the 1980s, Commander Pac Fleet paid for development & fielding of UHF comm relay installed in “blivets” to be buddy-stores on Navy tanker & buddy store aircraft: I don’t know if they were ever used. Office of Naval Research has developed Radio Freq & lightwave comm relay intended as packages for unmanned air vehicles: don’t know if the unmanned vehicle programs picked these up as optional configurations for unmanned vehicles to host. Has the Navy unmanned system “sail plan” been issued? Would love to get a copy even if it is draft, to see what it calls for in terms of networked data links and other info sharing features of unmanned systems.
Great to hear from the blog again,
If we only focus on a single topic from the book for a minute: 7) Being Situationally Aware. I believe we will find that this topic pertains to two issues a) The situations faced by the Information Infrastructure and those who protect it, and b) The situations faced by the operational community who rely on the information itself to conduct operations.
Focusing on the operational community, and the changes we have seen in training, Tactics Techniques and Procedures, as well as changes in the rules of engagement based on the availability of information, we must consider that the loss of even a portion of this infrastructure could prove significant.
Should the Operations community write a book, and build a similar list, they might start with such items as
1) Tiered decision making based on information availability and fidelity
2) System limitations in low/no bandwidth Ops
3) Using Organic assets to maintain situational awareness
4) …
While the nature of Naval Operations has ensured the Navy continues to focus on balancing Information Technology with Operational Control, I can’t say that the Army and Air Force truly understand the gravity of the situation.
Good points John. It certainly is true that the operators need to plan for the result of such cyber attacks. It is the reason ADM Willard’s push in this direction has been so useful in my opinion.
Marv, Good blog. This certainlay would work for humanitarian ops and the like. As I’m sure is obvious, we can’t expect to tie to shore communications when we’re in a major contingency and attempting to use the adversary’s infrastructure that we’re trying to take down. Maybe the answer is being to be able to bring in portable ISP sites to install rapidly on the beachhead — but with some kind of AJ component. Or get a relay established to the nearest friendly safehaven.
Also, watching the Attorney General’s comments this morning on how the huge body of classified information was assembled with the good intentions of interagency sharing and then released inadvertently by someone who didn’t understand all the single-agency ramifications, makes me wonder if we aren’t trying to build a higher fence around IA but failing to lock the gate.
D.
Don, good thoughts. I wasn’t so much thinking of a combat zone as all of the other operations Navy is engaging in. The Space Data capability I mentioned was apparently used in Iraq but I don’t know how successfully.
Marv,
Marvelous as always. To push the Maginot line idea a little further, there’s nothing quite like budget woes to make the newly deficient appear impregnable. We in DoD are coming off of a glut of new starts which will have their life cycle support tails. Funding for new initiatives will be increasingly scarce as the wheel turns as it always does. Your idea is little different than listening to all of the talk about budget reduction nationally while infrastructure rapidly deteriorates. [I see that Shanghai can now move more traffic than the top 10 US ports combined.] So, combine the historical precedents both in France and in our military history [e.g., post-Vietnam] add in a dose of political reality on the national level and, to me, there is little likelihood of a systemic change in approach that your blog suggests.
Your efforts are indeed noble and on the right track. Absent a realistic demand signal, however, I don’t see how your initiative obtains traction.
Good points Rene but my experience tells me that we more often make rational changes when the budget pressure opens our political apertures.
DISN.
Marv,
Focus on the terrestrial-WAN portion of DISN for the moment (ignore the satcom stuff for a bit).
20 years ago, to use your time scale, DISN was in the comms retail business. In Navy terms, there were something like 200 nodes served in the San Diego area alone. ‘DISN’ reached at least as far as the building router and sometimes all the way to the end system. Highly vertically integrated, fragile, and expensive.
And DISA operated three major enclaves: NIPRNet (or MilNet in the older DDN-speak) was unclassified and ran over one set of physical infrastructure. SIPRNet (aka DSNET) ran system-high at secret or higher levels and ran over an entirely different physical infrastrucrure. Additionally, DSN — Defense Switched Network, aka voice phone, ran over yet another (aging and increasingly expensive) infrastructure.
Today, it’s all one infrastructure. SIPRNet uses VPN (layer 3 encapsulation) to run its secret-high enclave within the NIPRNet infrastructure. Lots of TACLANES, no separate plumbing. And DSN has migrated to VOIP over the same DISN infrastructure (for most of us this is transparent — the PBX got rehomed, not our desk phones).
There is a potential brittleness here, but it’s not in the infrastructure. There’s little defense in depth, but this lack does not track to the consolidation of the infrastructure. Quite the contrary — the single infrastructure, as you noted, allows redundant connectivity so an anchor dragging up the cable off Egypt causes a hiccup but not a crisis.
The shortcoming to the defense in depth brittleness roots to using security tools at only one layer of the ISO model. We’ve put all the eggs into a layer 3 enclaving basket. It’s not wrong to use enclaving, but it’s wrong to use ONLY enclaving. Hint: look higher in the layer model — like layer 6.
Radio comms.
The engineering shorthand is 10e-4.
And the conclusion of the lesson is to never use radio comms when you can use terrestrial.
Today, even stodgy old DISN is provisioned with OC192 backbones — 10.6Gb/s. And it’s off-shelf COTS technology. And ethernet LANs are routinely provisioned at the same order of magnitude.
By contrast, today, the highest capacity commercially available radio-WANs deliver 1-10Mb/s of capacity. (There is an apples-oranges comparison problem here, a WAN needs to be measured on a per-footprint basis rather than per single user basis because it’s a shared medium. But we’re in orders-of-magnitudes here where that’s noise).
History, backwards. When I was a commo for the first time, the ship-shore circuits to Chris Barber’s commsta ran at 75 baud. When his routers (aka radiomen of watch) got the ship-shore traffic, they’d then put the tape onto the AUTODIN circuit which ran at the blazing speed of 64kb/s — four orders of magnitude again.
This 10e-4 ratio has stayed remarkably stable over the past 40 years.
History, forwards. But it’s going to get worse.
OC192 is regarded as ho-hum by the fiber optic technology geeks…. there are engineering problems, but add more laser diodes to one end of the pipe and more photorecepters at the other end and voila, more capacity.
But in radio-land, we’ve pulled a lot of capacity rabbits out of hats over the past 3 decades, improving the bits/hertz ratio. And there are a few tricks left that will help marginally. But we’ve just about exhausted the engineering tricks left; the remaining one we haven’t figured out how to solve is the physics trick: more bandwidth. S’far as I’ve been able to find, only God can make more spectrum and he didn’t do that any time recently.
Counter the argument if you can; I’m listening. But I foresee the 10e-4 ratio getting worse, not better.
Great Stuff Marv
Also some really good comments here
Navy tapping into “foreign ISPs” is certainly controversial, but no more dangerous than procuring food, fuel and repair services from foreign providers which deployed USN ships do as a matter of course.
Since the CNO has defined information as a “weapon” I would think its time for the Navy to begin to examine the idea of USN ships as mobile WiFi “hotspots” that can provide webbased services to forces ashore like it does with gunfire support and combat air patrols. I wonder if N2/6 has started to think about recommending replacing magazines with server rooms aboard Navy Warships?
joemaz
Marv,
These blogs and comments are rich in ideas, some of which I’ve been trying to get my head around for some time.
Contracting for data services just like we do other hotel services overseas scares me a little. While it would provide significant increase in capacity, how do we keep it secure? I believe that’s your point Marv. In a world where I am constantly being asked about “secure supply chains”, we certainly have some ground-breaking work to do before foreign ISP’s for our ships can make sense. Maybe the CANDID ACTD and the Virtual Secure Enclave work will help us here.
Joe,
using our afloat platforms as a mobile hotspot, however, is extremely interesting!
Like you, I also espouse the concept that the combat power of our ships will soon be measured by their computing density vice the number of its missile tubes. Little by little, I see this migration already starting.
dj
I am delighted to see you providing a thoughtful comment or two.
I have been ruminating about the future US Navy. While the picture is never clear, for a variety of reasons which include politics and money of course, what seems absolutely clear is that the operations of the Future USN will be critically dependent upon complex communications. These communications must never go down or be subverted. The flow of intelligence and operational information and control will be dependent on the system always working. I will not suggest how this is to be done; but if it is not done we will find ourselves unable to operate or coordinate effectively, and with possible catastrophic consequences.
Now that I have said that I am sure that you will solve it.
Thanks for the comment Lu. You are correct about the need for always available communications. My concern is that we are fooling ourselves into believing that we have that communications and therefore are not open to new ways of achieving adequate communications diversity.
Marv,
Another great posting. It made me think about a previous discussion about why the Navy has been historically different in comms since the days of sailing ships and how this difference in “disconnectedness” has driven innovation. We have always been a messaging culture with the difference in ways that our strategic decision makers (vice operational and tactical for shore based services), are often disadvantaged users. Much like power generation, perhaps a conservation thrust along with our bandwidth creation thrust is value added as well. Thanks again, looking forward to reading the book.
V/R
Kurt
Marv,
As always, I love to read your blog and in my opinion, it is NEVER too long. I always learn a lot; you are usually a few points off of main road and your ideas provoke me to think. Thanks.
Good article and thought provoking.
Diversity is generally good but can have a down side if it is a wrong kind of diversity. I am firm believer in defense in depty but here is another way to look at the Maginot line example if we are going to draw lessons for the cyber environment. The Maginot line was actually defense in depth, up to 25 KM. It was not intended to stop the Germans but to buy time for full French mobilization. It failed in its intended mission to buy time because 1) the French did not cover the Ardennes Forest with defenses (faulty understanding of the threat) and 2) the French relied on “diversity” in that they depended on the the Belgian fortifications (Fort Eben-Emael) which the Germans broke through with an innovative assault with the “new technologies” of gliders and shaped explosives. I believe that the Maginot line example is a better example of the dangers of outsourcing, bad assumptions/understanding, and not maintaining a technical edge. The type of diversity that the French needed was to have a complete French controlled defensive line (perhaps thinner but harder to go around with a capabile French mobile force to plug the holes. There is a reason some of our peer competitors are pushing hard to buy the undersea cables and put their switches around the world. When you play the highest stakes game, you want to use your deck and deal the cards yourself. Semper Fidelis, Jim
Jim, the important thing is that we have the dialogue on diversity as part of the Naval communications infrastructure… I don’t see much of that going on.
Marv,
Your thinking process is head and shoulders above the rest of the Defense Industrial Complex, with huge barriers to innovation resulting from a broken IT Acquisition process (see Bill Lynn quotes from the 09 Defense IT Acquisition Summit IT-AAC co-hosted).
As DOD’s recent Section 804 report to congress only addresses the oversight burden, we still need some improved mechanisms for speeding emerging technologies to the war fighter. I suggest we make this a key part of our Jan 10th IT Acquisition Advisory Council meeting. If you cannot attend in person, I hope you can dial in and offer your thoughts on how best to usher in new thinking into the DoD IT Acquisition Ecosystem.