 One of the hardest things to change in human society is a long-standing myth. The current well accepted myth about information technology (IT) systems is that they cannot be defended against well-funded, determined hackers. Because such myths are rarely questioned, the cyber security workforce takes it as a given that even highly secured IT systems will be compromised at some point. The good news is that myth-busting cyber technologies are now available to transform cybersecurity from today’s major government, financial, and consumer challenge, into a future where all but deep insider cyber intrusion is impossible!
One of the hardest things to change in human society is a long-standing myth. The current well accepted myth about information technology (IT) systems is that they cannot be defended against well-funded, determined hackers. Because such myths are rarely questioned, the cyber security workforce takes it as a given that even highly secured IT systems will be compromised at some point. The good news is that myth-busting cyber technologies are now available to transform cybersecurity from today’s major government, financial, and consumer challenge, into a future where all but deep insider cyber intrusion is impossible!
Current virus protection, firewalls, and newer high-technology variants of these boundary defense technologies do provide a measure of cyber defense-in-depth. They do not, however, fully protect against Tier V-VI level threats as shown in this graphic from the January 2013 Defense Science Board Report, Resilient Military Systems and the Advance Cyber Threat.
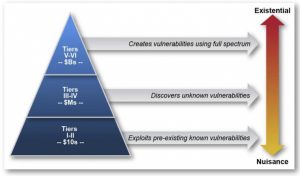 As described by this DSB report, hackers can be characterized as operating in the Tier I-II thousand-dollar club, the Tier III-VI million-dollar club, or the Tier V-VI billion-dollar hacker club. As shown, these hacker attacks broadly range from nuisance attacks to existential societal change attacks. V-VI Tier hackers are those funded through large countries led by United States, China, Russia, Iran, and, North Korea. These full spectrum attacks include equipment modifications through supply chain access, deep insider threats, advanced persistent threats (APT), and other techniques that break encryption or gain more than electronic only access. Tier III-IV hackers, funded through organized crime and smaller countries, are able to achieve disruption through malware including: phishing attacks, denial of service attacks, ransomware, and related attack variants. Tier I-II hackers use easily attainable dark-web tools, such as password crackers, to exploit known vulnerabilities generally blocked by virus protection, virtual private networks, and related tools.
As described by this DSB report, hackers can be characterized as operating in the Tier I-II thousand-dollar club, the Tier III-VI million-dollar club, or the Tier V-VI billion-dollar hacker club. As shown, these hacker attacks broadly range from nuisance attacks to existential societal change attacks. V-VI Tier hackers are those funded through large countries led by United States, China, Russia, Iran, and, North Korea. These full spectrum attacks include equipment modifications through supply chain access, deep insider threats, advanced persistent threats (APT), and other techniques that break encryption or gain more than electronic only access. Tier III-IV hackers, funded through organized crime and smaller countries, are able to achieve disruption through malware including: phishing attacks, denial of service attacks, ransomware, and related attack variants. Tier I-II hackers use easily attainable dark-web tools, such as password crackers, to exploit known vulnerabilities generally blocked by virus protection, virtual private networks, and related tools.
The exponential growth of cyber-attacks, as evidenced by newspaper headlines describing massive loss of our personal information, including credit information and passwords, is now a Presidential level challenge and has elevated cyber to a U.S. National Security warfare area. Not often discussed or considered is the fact that every cyber malware attack must borrow a Computer Processing Unit (CPU) instruction from the attack target system in order for attacking software to operate the malware instructions! In the physical world equivalent, such as bank robberies, criminals must borrow access to city streets, bank buildings, and bank vaults to conduct successful robberies. Fortunately, in cyber space, new synergistic technologies are now available to prevent malware from borrowing CPU instructions, thereby significantly enhancing cyber defense-in-depth. Unfortunately, most organizations are reluctant to purchase this enhanced cybersecurity because they are confused by all of the cybertool hype and fall back on the mythology that persistent cyber intruders will always win so what they have is good enough.
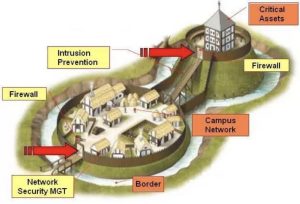 Medieval walled castles can be thought of as a physical representation of today’s cyber security situation. Although high walled castles provided good city defenses for over 900 years, they quickly became obsolete as the synergistic inventions of gunpowder and cannons spread in the 14th century. Until then, castles were effective at keeping out most small intruder gangs, but were unable to prevent a persistent siege from a large army that could eventually cross over, under, or through castle moats, walls, and gates to breach walled cities. Likewise, today’s IT system cyber boundary-defenses slow down cyber hackers but do not completely stop persistent and well-funded hackers, working over long periods of time. Just as castle moats, gates, and walls were no match for the gunpowder and cannons of the 14th century, current cyber boundary defenses are no match for today’s advanced persistent cyber threats. Just as walled cities gave way to modern active defensive weapons, cyber boundary defenses must now give way to more effective cyber-technologies.
Medieval walled castles can be thought of as a physical representation of today’s cyber security situation. Although high walled castles provided good city defenses for over 900 years, they quickly became obsolete as the synergistic inventions of gunpowder and cannons spread in the 14th century. Until then, castles were effective at keeping out most small intruder gangs, but were unable to prevent a persistent siege from a large army that could eventually cross over, under, or through castle moats, walls, and gates to breach walled cities. Likewise, today’s IT system cyber boundary-defenses slow down cyber hackers but do not completely stop persistent and well-funded hackers, working over long periods of time. Just as castle moats, gates, and walls were no match for the gunpowder and cannons of the 14th century, current cyber boundary defenses are no match for today’s advanced persistent cyber threats. Just as walled cities gave way to modern active defensive weapons, cyber boundary defenses must now give way to more effective cyber-technologies.
Like the synergistic technologies of gunpowder and cannons, the key to hack-proof cyber security is new patented technologies that synergistically integrate robust encryption, high-performance computing, and virtualization. Using these technologies can eliminate all but deep-insider threats, thereby eliminating all but the most persistent Tier V-VI cyber-attacks. The castle equivalent of this cyber security technology would be hiding all castles behind invisibility cloaks to prevent attackers from moving to, into, within, or from a walled city.
So, what’s so different about combining encryption, high-performance computing, and virtualization to eliminate cyber security threats? Encryption has been used for thousands of years as a method to hide information, plans, or other secrets. As computer performance has improved, so have the strength of encryption techniques and the competing cryptology techniques to break encryption. Strong encryption, however, remains one of the most effective ways to prevent hackers from obtaining useful information, be it in transit, or stored in databases and backup storage media. Now, thanks to the Trusted Computing Group consortium, Trusted Platform Module (TPM) chips can be embedded on computer server boards, to provide NSA approved strong encryption on all server and desktop CPU motherboards.
 The problem is that all but the most modern data centers contain extensive cyber threat opportunities because CPUs are used to enable the functions of every major data center subsystem including servers, storage systems, network devices, and supported desktops. Each of these subsystem CPUs provide hackers the threat surface to borrow CPUs for their malware. In addition, even though TPM chips, providing strong hardware based encryption, have been available for a decade, these optional chips have been largely ignored by IT manufacturers because the “everything can be hacked myth” argues against the small extra system cost and TPM setup administration. What is changing this situation is the rapid growth of Software Defined Data Center (SDDC) technologies that enable fully virtualizing modern data centers. A fully virtualized SDDC forces all application, server, storage, network, and desktop functions, to operate under a single set of server CPUs thereby eliminating all independent storage system CPUs, network system CPUs, server CPUs, and fat-client desktop CPUs.
The problem is that all but the most modern data centers contain extensive cyber threat opportunities because CPUs are used to enable the functions of every major data center subsystem including servers, storage systems, network devices, and supported desktops. Each of these subsystem CPUs provide hackers the threat surface to borrow CPUs for their malware. In addition, even though TPM chips, providing strong hardware based encryption, have been available for a decade, these optional chips have been largely ignored by IT manufacturers because the “everything can be hacked myth” argues against the small extra system cost and TPM setup administration. What is changing this situation is the rapid growth of Software Defined Data Center (SDDC) technologies that enable fully virtualizing modern data centers. A fully virtualized SDDC forces all application, server, storage, network, and desktop functions, to operate under a single set of server CPUs thereby eliminating all independent storage system CPUs, network system CPUs, server CPUs, and fat-client desktop CPUs.
By thinking differently about how these synergistic IT technologies can be utilized differently to secure IT systems, several small startup companies are moving IT systems from walls and moats to modern active cyber-defenses. One startup company* has patented Hyper Converged Infrastructure (HCI) server technologies that synergistically integrate high-performance computing, TPM hardware encryption, and SDDC virtualization to prevent all externally introduced malware from obtaining CPU instructions, and thereby exposing and preventing any malware from operating. After verifying all startup software is valid and clean of malware (attested), any malware introduced into the data center through phishing attacks, denial of service attacks, and all other hacker attacks including zero-day attacks, is immediately exposed and recognized as non-authorized software when an unattested CPU instruction is requested. That instruction is then automatically moved into a shadow netw0rk for observation and analysis while the SDDC continues functioning normally.
But what happens when a SDDC is inadvertently or maliciously attested with embedded malware, or what if the software is only operated within a commercial cloud service infrastructure? Another startup company** has addressed this problem by creating an encrypted metavisor shield surrounding the guest operating system and all application VMs or application containers. The metavisor, using encrypted communications both ways, is transparent to the guest cloud system because it presents itself to the guest OS as the cloud hypervisor, and to the cloud hypervisor as the guest OS, thereby enabling process integrity checks that are abstracted into the independent metavisor layer. The metavisor monitors system instruction or memory calls for abnormal activity and alerts system administrators if the system is compromised and needs to be re-attested.
When these technologies are combined, even greater cybersecurity is available by creating a hybrid 0n-prem/cloud deployment that securely manages all root encryption keys on-prem, and securely extends those root keys to the in-cloud guest operations. This is accomplished by augmenting the on-prem HCI SDDC with the encrypted metavisor layer to ensure that any SDDC insider attack (inadvertent or malicious) that introduces malware into the attested SDDC is again captured and observed prior to operation.
Top White-Hat hackers, have tried to hack these technologies and agree that when properly set up, such an SDDC cannot be hacked without indavertant or malicious insider attacks to install and attest malware into the system.
This integrated combination of new technologies fully supports the secure deployment of multi-cloud and multi-platform IT environments by further abstracting VMs or containers away from the physical hardware infrastructure on any release of Amazon Web Services, Microsoft Azure Cloud Services, Google Cloud Platform, or other commercial cloud providers.
Given the increased sophistication and prevalence of today’s cyber-attacks, even the best perimeter defenses can’t stop hackers from gaining access to corporate or government datacenters.  When that happens, these new synergistic technologies prevent attackers from borrowing CPU instructions and extend that protection into commercial cloud services by abstracting all cloud guest activity across the encrypted metavisor to prevent malware from compromising the system or exfiltrating data.
When that happens, these new synergistic technologies prevent attackers from borrowing CPU instructions and extend that protection into commercial cloud services by abstracting all cloud guest activity across the encrypted metavisor to prevent malware from compromising the system or exfiltrating data.
This post has only covered the bottom layers of IT infrastructure. The next post will extend this discussion by introducing new technologies that protect encrypted data and transaction ledgers, riding upon the SDDC and cloud infrastructure layers.

Thanks Marv,
Even to tech impaired person like me the approach you have presented makes sense. Hopefully others that can implement this approach will take notice. We are wasting a lot of time and resources to defend our IT world, that could be used to make IT infrastructure work better at making the world better for everyone.
A truly excellent piece Marv! Very well written and referenced, I will have to read it a few more times for it to sink in. It is so encouraging to see all this good work being done, and much of this is very bio-inspired, though the biologists and the cybersecurity folks still don’t talk as much as I think they should.
From my perspective, learning more from the immune system is a key way we’ll get to really high performance cybersecurity. I call bio-inspired machine intelligence (like deep learning and affective computing) Natural Intelligence, which I think is an even more useful term than AI, and bio-inspired security has been called Natural Security for about ten years now. It is an exiting and still little-known approach to security. A good foundational book is: https://www.amazon.com/Natural-Security-Darwinian-Approach-Dangerous/dp/0520253477/
Stephanie Forrest’s work on Artificial Immune Systems in the 1990s pioneered that perspective for cybersecurity. Melanie Moses at U. New Mexico is one of the current leaders in that work. She’s presently applying immune systems metaphors to biosurveillance for disease control and management, but her approach can be generalized to all kinds of collective social and technological defense work. See her 2017 paper: http://ieeexplore.ieee.org/document/8285356/
Keep up the fantastic work and I look forward to the next post in this series!
Warmest Regards,
John
John, thanks for the great reference material and comments. When I led a DARPA division for a short period in the late 90’s, the DoD’s first R&D on cybersecurity was initiated under a brilliant project manager named Sami Saydjari. His project was based on building cybersecurity that would emulate our immune system. I often gave talks in those days saying that mother nature protects our bodies using as many cells dedicated to our immune system as she dedicates to our brains – about 10 trillion cells each if I remember correctly.
Marv,
A good beginning argument for bringing the power of AI to bear on the Cyber Security domain. Once again you bring your uniquely qualified thoughts to the challenges we are facing now and in the near future.
Ben Apple PhD