Now that we have a new administration readying to transform the Executive Branch, it is the right time to reverse decades of inefficient DoD acquisition!
Because cyber vulnerabilities are pervasive, today’s acquisition challenges are even more complex than the challenges of twenty years ago. If our military systems are to remain effective at deterring and repelling foreign aggression, cybersecurity and cyber resilience must become an overriding consideration!
Recently RADM David Lewis, Commander Navy Space and Naval Warfare Systems Command, spoke at the annual Navy aviation Tailhook Association Symposium. He opened his talk by telling the audience… …your grandmother was right, there really is a boogeyman under your bed, and that boogeyman is cyber vulnerabilities hidden in the millions of lines of software controlling your airplane and weapon systems.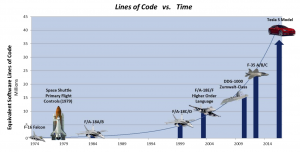
As shown by RADM Lewis’ graphic above, software driven computer control permeates everything in our modern world, and for good reason. We consumers enjoy efficient and effective products at attractive prices because the exponential  growth of IT performance, coupled with reductions in IT cost, makes it logical for design engineers to embed IT into all products, from refrigerators to automobiles. That leaves only one small catch! All products and systems are now subject to cyber security attacks! A well published example is the hacked Jeep being remotely driven off the road as publicized in Wired Magazine even back in 2015.
growth of IT performance, coupled with reductions in IT cost, makes it logical for design engineers to embed IT into all products, from refrigerators to automobiles. That leaves only one small catch! All products and systems are now subject to cyber security attacks! A well published example is the hacked Jeep being remotely driven off the road as publicized in Wired Magazine even back in 2015.
 So why haven’t previous reform attempts and current DoD reforms improved acquisition effectiveness? The simple reason is that all previous and current reform initiatives have not effectively addressed the following counter productive realities:
So why haven’t previous reform attempts and current DoD reforms improved acquisition effectiveness? The simple reason is that all previous and current reform initiatives have not effectively addressed the following counter productive realities:
- Centralized bureaucratic oversight – continuing to bloat decision timelines, increase system costs, increase program schedule, and reduce system performance;
 Color of money – slowing down development, and in turn forcing good people to invent creative time consuming ways to work around these rules;
Color of money – slowing down development, and in turn forcing good people to invent creative time consuming ways to work around these rules;- High checker to doer ratio – enabling checkers to overwhelm development and fielding decisions throughout the acquisition lifecycle;
- Time is money – exponentially increasing program costs in the name of taxpayer dollar stewardship, with the unintended consequence of delaying capability to the warfighters;
- Growing cyber vulnerability – permeating all system IT hardware and software, while cyber resilience continues to be treated as an afterthought; and,
- DoD IT and cybersecurity arrogance and ignorance – ignoring best commercial products and practices, while remaining years behind state-of-art cyber resilient IT technologies and products.
Based upon my 40 years of acquisition experience, I believe focusing on these three primary acquisition antagonists would mitigate these challenges:
- Acquisition oversight must be returned to Service level military control where speed to capability is a cultural imperative;
- Cyber security and resilience must be continuously verified rather than pacified by paper processes that leave developing and operational systems vulnerable to hackers; and,
- High checker to doer ratio must be reversed to mitigate oversight second guessing by enabling trusted, but accountable, short decision cycles.
To address these realities, let’s discuss cyber security and resilience first, because these changes could be put in place with very little Congressional involvement.
The good news:
- Cyber Commands have been stood up at the National and Military Service levels to actively support cyber defense, cyber offense, and cyber support to military operations;
- Military Operational Test & Evaluation (OT&E) commands have gotten much more engaged in cyber resilience testing which is now included, to some degree, in all system testing;
- Cybersecurity funding has increased significantly over the past decade; and,
- Cyber certification prior to system installation and operation is now the norm.
This good news, however, is overwhelmed by:
- Ineffective cyber certification processes further slowing development and fielding timelines; and,
- Fast growing commercial cyber security and resilient IT hardware and software not being quickly adopted, while DoD attempts to sustain, across its systems, end of life hardware and software.
The President’s new administration could reverse this reality by rapidly implementing the following changes at DoD:
 Transform cybersecurity from a bureaucratic approval process into continuous or at least daily penetration testing (pentesting) and random red team activity across all DoD/IC operational system and infrastructure components.
Transform cybersecurity from a bureaucratic approval process into continuous or at least daily penetration testing (pentesting) and random red team activity across all DoD/IC operational system and infrastructure components.- Merge DoD’s Chief Information Officer (CIO) and the Principal Cyber Adviser (PCA) positions into a single senior military CIO position, reporting to the U.S. Cyber Command, and assign senior military officers as Service CIOs, reporting to each Military Service Cyber Command.
- Authorize secure/resilient cyber IT system operations following successful independent OT&E pentesting conducted by DoD and Service OT&E testers, using CIO approved pentest tools.
- Require daily operational IT system and infrastructure pentests under the responsibility of operational commands, using CIO approved pentest tools.
- Conduct random unannounced red team events across all DoD systems and infrastructure, conducted by the Cyber Commands.
- Break apart the Defense Information Systems Agency (DISA) into a cyber resilient IT acquisition command, and an operational command reporting to U.S. Cyber Command.
The other acquisition antagonists, oversight reform and checker doer ratio, must be addressed from two interdependent but integrated perspectives; 1) platform/weapon acquisition, and, 2) resilient cyber IT system and embedded IT system acquisition. These changes must be supported by Congressional modifications to the Goldwater-Nichols law building from the recent good work of Senator McCain:
- Eliminate centralized civilian acquisition control by re-establishing Military Service level acquisition control for all Service acquisition programs, reporting to each Service Chief; and, senior Military acquisition control for DoD Joint and Intelligence Agency acquisition programs, reporting to the Chairman of the Joint Chiefs of Staff (CJCS).
- Eliminate colors of money across the DoD budget, allowing program managers the flexibility to apply all resources when and where most needed.
- Adopt “speed to capability” as the primary acquisition metric for all programs across the DoD/IC and Military Services; measure performance and promotion for program managers, contracting officers, acquisition legal counsel, and financial budget personnel against speed to capability support.
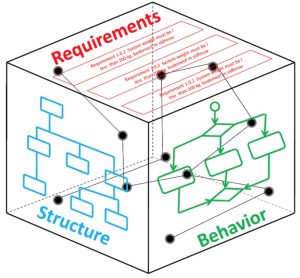 Apply “Model Based Systems Engineering” automation tools to all acquisition programs using a DoD standardized tool set.
Apply “Model Based Systems Engineering” automation tools to all acquisition programs using a DoD standardized tool set.- Assign program managers the authority and final responsibility for decisions that conflict with contracts and legal support.
- Consolidate and collapse acquisition oversight staffs under the CJCS, and eliminate all or most staff positions from the DoD Undersecretaries of Acquisition Technology & Logistics, USD(AT&L), and Intelligence, USD(I); likewise for each of the Military Services.
- Eliminate most acquisition oversight decision meetings by remotely monitoring “model based system engineering” automation tools; require meetings only when automated tools indicate high program risk or failure conditions.
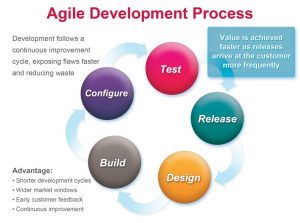 Establish and iterate cyber resilient IT requirements using the “IT Box” process continuously adjusting requirements to support operational needs; rapidly adopt new technologies that improve cyber resilience and/or operational capability.
Establish and iterate cyber resilient IT requirements using the “IT Box” process continuously adjusting requirements to support operational needs; rapidly adopt new technologies that improve cyber resilience and/or operational capability. - Acquire all IT using short cycle agile development processes and continuous user interaction to deliver partial capability and upgrades on six to twelve month cycles.
Many would argue that DoD must be evolutionary and these suggested changes are too radical!
Decades of past and current acquisition reform, however, have delivered little value add while our military technical superiority, more than ever, is being challenged by today’s hostile and competitive global environment! Without changes like these, our Country is saddled with a DoD that pays lip-service to taxpayer stewardship, while squandering people and dollar resources on bureaucratic acquisition waste, and in response, asks its warfighters to do more with less.
 At the same time, U.S. military operations have proven to the world that information dominance is a critical warfare discriminator, yet DoD acquisition worst practices are pushing U.S. military IT capabilities backward while commercial information technology is accelerating into adversary systems. For example, space based tracking and imaging, global mapping, and big data processing, are now available to anyone for a price, further eroding our U.S. military advantage.
At the same time, U.S. military operations have proven to the world that information dominance is a critical warfare discriminator, yet DoD acquisition worst practices are pushing U.S. military IT capabilities backward while commercial information technology is accelerating into adversary systems. For example, space based tracking and imaging, global mapping, and big data processing, are now available to anyone for a price, further eroding our U.S. military advantage.
Now, as we enter the age of autonomous vehicles in the air, undersea, and on the surface, U.S. military advantage will continue to be eroded unless something is done to turn this tide.

Marv,
as always I agree with your well thought through points. I especially resonate with getting rid of the “color of money” restrictions and reduction of needless bureaucratic oversight. My personal experience is that alone would free up 50% of a Major PMs available duty cycles. Cycles better used actually running his or her program!
I would also like to add another nuance to the discussion.
It’s well understood that one of the reasons why our Acquisition processes are not optimized for modern C4I and Cyber programs is that they were designed to support the development and fielding of traditional platforms (ships, subs, aircraft). Looking through the lens of RADM Lewis’ chart, however, we should start looking at our platforms as nothing but physical containers for hosting software capabilities. Yes those platforms are very expensive, high tech steel and composite, but the reality is that everything is a software program and subject to the foibles of software development; not treating it as such is leading to some of our most visible and embarrassing failures.
DJ,
I agree. If I may expound a bit on your proposed change in perspective with regards to platforms and Marv’s thoughts…
From a cyber perspective one could argue it comes down to 3 facets.
THE ENEMY GETS A VOTE.
The enemy is not static. The enemy doesn’t simply go off and do what you want them to do. In fact, they go to great lengths to do just the opposite! You cannot control the enemy. They are intelligent, resourceful, and they get a vote. They are going to respond to any action on our part that benefits us with a reaction that benefits them. We need to acknowledge that vote. The point being the defensive environment is ever-changing.
The second thesis is…
THE SYSTEM IS THE BATTLEFIELD
Since cyber is so inherent/embedded within the COTS-IT environment the current de-facto mindset is that if you increase the rigidity, control, and multi-layer IA oversight of the acquisition you are also controlling the “battlefield.” Total battlefield control via acquisition is a false sense of security and a facade.
Since the “system is the battlefield” to slow the pace of acquisition and COTS-IT change simply concedes the military concepts of “weapons superiority” and “maneuver” to your opponent. It is highly doubtful that a military tactician in the physical world would recommend this, those elements are taught to every cadet/midshipman, and is a principle as old as the teachings of Sun Tzu. Yet do we still see that concession around us every day?
The last thesis is….
YOU’RE ALREADY AT WAR
If we believe this to be true in cyberspace then that reality, in of itself, is a complete change of mindset. I submit no battlefield commander at war thinks in terms of stopping weapons development, adding layers of bureaucracy, and diluting the decision-making process in order to succeed. Just the opposite. The pace of innovation accelerates, the decision-making process is streamlined, oversight is replaced with accountability, and the situation is acknowledged to be highly dynamic and beyond the combat leader’s total control. So if we’re truly already “at war in cyberspace”; are the current acquisition processes and changes congruent with the desired outcome?
We need to recognize that without a sea change in this area the current processes and impediments, from a war-fighting perspective, could be adding to the likelihood of an existential cyber event..not preventing one.
To Marv’s premise it’s time to stop thinking of this war-fighting landscape simply in terms of budgets, milestones, and oversight. We need to recognize that THE ENEMY GETS A VOTE, THE SYSTEM IS THE BATTLEFIELD, and YOU’RE ALREADY AT WAR.
Respectfully
These are important suggestions that cannot come soon enough.
I am not a DoD acquisition expert, but do know cyber security. It is clear that the current situation must be addressed and urgently and radically.
Marv, this is an excellent piece. I am curious to know what reactions this willr aise from the current DOD Acquisition and IT leadership teams.
Excellent discussion Marv. The acquisition process needs to be agile and cybersecurity threat management needs to permeate every step in the process.
Excellent.right on target…the only I would add is a for IT DOD must adopt a spiral development model like ARCI with annual deliveries (or less) to address the changing IT and Cyber environment.
The Iphone which represents the middle of the market technology has had 7 generations since it was introduced in 2007 with 4 generations of infrastructure improvements in parallel to support these devices. In the wireless communications business there are 5 major players (2 Chinese) and thousands of resellers and innovating companies which because the entire architecture is standards based, are able to leverage the technology to build thousands of capabilities, quickly.
We must also address this standards based process and allow independent development for DOD IT architectures and allow all developers to effectively participate in the acquisition process.
Marv–the top of the service acquisition pyramid is based on OPNAV requirements officers doing a 2 year tour. These RO’s do the best they can but are consumed by daily fires and have limited tech knowledge. This short term view is pushed to program managers that are highly restricted by the acquisition regulations you mention. The Navy should emulate the model of the Submarine Security Program. This program used the technical support at JHUAPL to stay ahead in submarine warfare. The same should be done with cyber–bring in a trusted partner to take the long view and to help OPNAV with tech support. You can’t fix acquisition unless you have OPNAV making the right plans and funding decisions.
Wayne, great points. Because CNO has reorganized again to help address some of these OPNAV issues I didn’t try to address that yet but it is a part of the challenges. Thanks
What and how.
Marv, many of your suggestions (with which I have little quarrel) have to do with the _how_. But we need to worry about the object that needs to be secured.
Too often, the object being secured is a computer (e.g. password fascists). Or an enclave within the internet (e.g. VPNs, SIPRNET). These are infrastructure protections. What they are not is content protection. An example of content protection is e-mail signing and encryption:
– the scope is end to end, not just partial (many UAs store mail on the computer in the original (e.g. encrypted) form. In ISO Reference Model terms, this is layer 6/7 protection.
– layer 7 protection is independent of the security of the infrastructure (which may or may not be a bad idea, but is a different subject).
Too often, we zealously apply a solution that is not targeted at the problem.
Marv,
Looking at the changes you would want the DoD to make with acquisition is spot on. Right now I am fighting an issue with getting funding through to make procurement and place funds on task, and contracts is holding it up because of literarily one word. Also item (9. Agile Development) is starting to get a little long in the tooth; the better direction is in Continuous Delivery and Continuous Integration. And testing can be automated within the CDCI process. Let’s automate as much as possible. You also said something that is another key point and that is culture, we have to change the culture for your changes to take hold; we have to change the “Frozen Middle”.
Thanks JR, spot on… We need to keep working this no matter what the administration does or doesn’t… marv
Marv,
Great post! Concur and hoping these changes can come to fruition with the new administration.
HT
Marv,
You’re spot on! I would like to add that the common element throughout your discussion is the decision maker. We, DoD, have a problem of appointing folks to acquisition decision making positions without the right technical qualifications to have an understanding of the nuances of the highly technical problems the capability of the combat system being acquired is attempting to solve. Basically, the reason for all the acquisition decision milestones is to give the PM’s some time to have contractors, who by the way do understand the technical nuances, review the technical material and give the decision maker the confidence he needs to approve the continuance of the acquisition program. All these reviews and sub reviews and reviews of sub-sub-reviews cost $$ and take time. Meanwhile the system’s new expected capability atrophies and/or is rendered obsolete due to a new technology that is introduced.
It almost seems that when and if ever DoD’s tech vector tends to overcome industry’s tech vector, that’s when the DoD Acquisition process will recover — suggesting that DoD should be investing heavily into R&D and learn to accept failure in 70% of the R&D. (Aside: I just picked 70% out of my more than 40 years of observing the DARPA, SERDP, ONR, and all other labs R&D process and success rate for the application of R&D $$ to a DoD problem.)
We first have to get some technically qualified people who are not afraid of firing incompetents in the acquisition pipeline. I think that hiring technically and operationally qualified people the first step to repairing the needed introduction of Cyber (an area few, even smart, people truly understand) into the acquisition process as well as streamlining the acquisition process. Once we have qualified people in these critical DoD acquisition positions, perhaps we will be able to focus on some REAL R&D for DoD and diminish our reliance on industry which leads a profit driven R&D investment strategy.
Marv,
Your thoughts will certainly enhance the rapid adaptive nature of matching acquisition to the constantly evolving environment, where some of the past program completion durations are counted in years, and often tens of years.
However, material infrastructure hardness against cyber intrusions that we can buy or build quickly may only be part of the answer. The threat paradigm may have shifted. There is also a need to solve the “not in my swim lane” technical culture as much as ” the color of money” in the program management. A method of effective inter program technical liaison is also needed. For example, current commercial innovation enables high school kids to spoof GPS for Pokemon-GO waypoints in a non intrusion manner. This is further in technical advancement than the high school kid phishing method for intrusion based Internet access. There can be inter-program technical concerns not in the “swim lane” but they are in the swimming pool.
Marv, Great perspective and great recommendations. I fully support and will do my best to assist in advocating for change as quickly as possible.
Marv,
Very good article, with strong, reachable and actionable recommendations.
On the “getting it built” side of the house, I would recommend you highlight the current state of Government Lead System Integration (LSI). Most of our Gov Lead LSI projects are not progressing/delivering, but are consuming and executing at very high costs to the DoN.
We all know that Government currently cannot train the workforce fast enough to keep up with the latest C4ISR “Digital” enabling technology. Also, our Echelons III’s and Labs tend to build their business models based on the last technology they have mastered, created a lab for, and written into their spend/personnel plans for. As a result, new technologies are not only disruptive (which is normal everywhere), but existential threats to the working capital activities, which combined with the insider seats they have in all ECH II Project Offices, creates strong anti-bodies to new technology transition/insertion/migrations.
This pattern creates unintended consequence tends to create a culture of “tenured incompetence”, that is supported by mandates to keep “ALL” employees occupied, not necessarily those qualified, trained or competent to execute.
I see that issue highlighted in your “Checker versus Doer” analogy, in which our Labs, Warfare and System Centers can provide dozens of Checkers, but very few doers. The access to ECH II budgets and “POR” inside information also pre-empts “non-competitive” systemic fixes, like replacing Contractors/Teams that do not perform.
So assuming that a Requirement survives the long validation and oversight processes you discuss, and that we get the resourcing, then this “built it” tenured and inside personnel end up executing very large level of efforts doing processes and checking, but not building and delivering. The LOE typically/coincidentally matches what resources the APM or Project office has in the check book, and past performance is typically not a factor. That also contaminates the supporting LSI Contractors, since they also typically stay behind their Leads, and are content/resigned to be “highly paid” but delivering very little.
The size of an Gov LSI team (again, size is THE highly rewarded and incentivized metric in FITREPS and EVALs) then grows with ratios of 10 to 1 checkers to doers, and those teams are typically not even qualified (other than having access) to execute the work tasked; since they were typically on the bench when new Tech arrived. All of this then drives “Delivery of Capability to the Fleet” toward a tertiary status, behind LOE and On time Expenditures of different colors of money.
Hopefully the DoN will recognized all these issues and patterns, as we attempt to pivot towards an Enterprise that actually delivers faster than our adversaries. Three recommendations I see, from a getting it “built and delivered” perspective would be:
1-Any personnel (GOV or CTR) would have to sign NDA’s and OCI memo’s when working the ECH II offices. This would protect competition, lower costs and guarantee transparency when an project would move towards execution. No one should have the budget for a project prior to , if you are bidding a project.
2- LSI, Development and PMP projects bid by Government Entities would have to show actual current competency/personnel for the work bid, along with positive past performance (akin to CPAR’s). Use the current CPARs system to create a GPARs system.
3-Make Competency, speed to capability and past performance the key variables for award, not tenure.
VR
Nando
So very true….
Marv,
Good morning. Your update is essential, especially your “high checker to doer ratio” concern. Would offer that both productivity (time to solution) and performance (speed of data processing) are the critical measures where programs should focus in competitive proofs of concept to select commercial or gots products upon which to build solutions. Best wishes. Dennis Dalton
Marv,
I always enjoy your posts. What I fear most in any scenario to “fix” the current broken acquisition system is the readiness of the workforce to martial said “fix”. I urge folks to look at this work by Joseph Kasser (and colleagues) on the five types of systems engineers. Quoting Kasser:
“Types I to III are levels through which a person grows with education and experience.
The debate on ‘nature’ or ‘nurture’ comes into play at Levels IV and V. However,
irrespective of the debate, it is important to identify people with the potential to
become Type IV’s and V’s as early as possible in their careers and then to provide
them with fast track training to enable their organization to obtain the best use of their
capabilities in the future”
Our current government bureaucracy has not done well at identifying and cultivating type IV’s and Type V’s. The result, we lack the critical skillset to drive the revolution to conclusion(s). Along with process “refresh” we need to also demand and go through the painful process of workforce “refresh” as I fear we are well past the point of work force re-training as a means to achieve this end.
Heresy? Maybe.
Just one mans’ opinion. Perhaps this is but one dimension of the more doer less checker model?
Outstanding article. I always enjoy reading your focused comments.
I look forward to more.
Marv:
You are too gentle. Pull the gloves off and speak the truth.
President Elect Donald Trump might be able to do what no other President has done: Drain the swamp filled with DoD knuckleheads who keep their jobs because no other President has fired them.
It is rich to hear the RADM in charge of SPAWAR talk about software. Wow. How many projects have been delivered on-time, on-budget that meet functional requirements on his watch? Zero. He is a shipyard guy stuck into a software factory filled with people who can’t get jobs in the commercial world.
While you cite agile as a solution, it is really only a method. And it is outdated. Tesla, Uber and the teams building >1 million lines-of-code apps don’t use agile. They use continuous deployment with scrum teams of 3 to 7. Meanwhile, RADM Idiot and his friends in the government still use waterfall methods requiring teams of 100’s. And they use ancient programming languages.
The core problem with the DoD is they exist as a jobs program for incompetents. No one ever gets fired for doing a bad job. Case in point: SPAWAR spent $8 BILLION on JTRS and had nothing to show for it. SPAWAR boast of generating 800 or so patents (over the course of a decade where they spent in excess of $50 billion). By comparison, Qualcomm wins 800 patents per quarter while spending less than 1% of SPAWAR.
The commercial world is light years ahead of the government in almost every aspect of technology. Why? We fire people who do not perform. The commercial sector has evolutionary pressure that drives innovation. The DoD has bureaucratic structures to protect incompetents.
It gets worse: Yes, we are at war. And the Chinese, Iranians and fat kids hacking in their parents’ basements in Russia are winning. No, the DoD will not (and cannot) win. The best and the brightest no longer want to work for the government. They work at high-tech startups that refuse to sell to the government. So the government is left to fend for themselves against forces that are far superior intellectually, technically and operationally. Case in point: OPM “lost” personnel records of more than 23 million people with security clearances. Anyone get fired? Yep. 1. The jackass OPM administrator who had the audacity to claim she was not responsible.
The SOLUTION:
First, start by FIRING 30% of the DoD civilian workforce. Slash their budget. Make them smarter by starving them. Cutting such a large portion of the workforce will have 4 consequences that will improve national security: 1) the DoD will not be able to spend so much time dithering with acquisition rules. They will be forced to streamline. 2) The DoD will have evolutionary pressure to weed out the incompetents. 3) Make it possible for the government to acquire the best technologies because the best companies will not have to deal with bureaucratic red tape and incompetent government employees. 4) Financial solvency for the government.
Second, STOP using the DoD as a jobs program. Get rid of the programs that protect 8A and every special class of retard that wants to win a government contract. Award to the best and the brightest. No one should care if the developer is a woman, veteran, purple or whatever. Only two tests: Price and Performance. Nothing else matters.
Good and straight forward comments from an anonymous source but A Patriot. Much of this is harder hitting than my more gentile post. I have said for years that we should send half of the people in the Pentagon someplace else or downsize them. More people in an organizational function, by definition, means more bureaucracy. And the government should become an organization that can fire people more easily. It used to be that government always meant smaller pay than commercial but not so today. On average government workers bring home more dollars than commercial for equivalent jobs. When the benefits are added it easily tops commercial compensation. And ad the writer states, nobody is ever really fired. In the acquisition business, we take so long to complete a program we can’t pin the cause to any one person because the POR may have had 4 PMs during the development and initial fielding period. Thanks for hitting hard.
There are several tautologies in this post, so -10 for style.
Starving the DoD will consolidate funding at echelon II and higher, further entrenching the programs of record and deprecating rapid deployment capabilities under development… so that won’t work.
Venture funded ‘high-tech’ startups have a failure ratio of 13:1, that’s depressing and taxpayers would reject a 13:1 software application success ratio for DoD products.
‘evolutionary pressure’ in commercial is inclusive to profitability. Success comes from market reach, penetration and ability to scale. Often, consumer based applications are littered with security flaws after reaching millions of users (**cough** Yahoo! **cough again** Target). Turbo Tax is a highly effective piece of software–let’s agree on that Ok? What do you think was spent on it’s development since the early 2000’s? I’d say in the ballpark of $20 billion, maybe more, maybe a little less. Do you think taxpayers would be ok with spending $20 billion on a desktop app or web-app? They freaked when they learned the Obama care website cost $450 million.
I’m not sure you know what Agile is? Scrum teams are part of Agile methodology.
Your Qualcomm analogy doesn’t fit here. Qualcomm has a fiduciary responsibility to protect it’s intellectual property. SPAWAR is under no such obligation and caters to hundreds if not a thousand unique customers. More often than not, refreshing existing tech.
I agree the DoD is largely a wasteful job’s program. I don’t think the brass or retiring brass should be put in charge of massive software development activities as you so eloquently stated. JTRS was by any real measure a colossal failure, so +10 there.
Some observations:
1. The government acquisition community does need to move faster but, unlike Apple, cannot start with a single new (computing) platform, but must work with many legacy systems fielded on many different warfare platforms, including systems that we do not own and are themselves constantly changing, while also working in an almost impossibly stilted funding environment, and addressing security risks that can impact national security. AND each program works for an individual office, not for a single head of a corporation with an actual vision and architecture (at least not yet).
2. OPNAV does need to define an integrated capability as opposed to defining individual system capabilities.
3. OPNAV does have to ensure that integrated capability is aligned or supports other DoD and external requirements, mandates.
4. Security cannot be defined by the individual acquiring Program Offices, but must be DESIGNED and BUILT-in.
5. Even the fastest spin-off of capability needs to be designed and documented. Designed to support specific capability requirements (and fix specific bugs) AND to meet defined security objectives.
6. Testing is critical, but cannot possibly find all issues, even all major issues. Even for the smallest of capability builds, good upfront design is worth the time because rework and re-integration (involving multiple PoR) is far more expensive.
7. Patriots may believe that government workers are highly-paid duds, but for the most part, that is not the case. For the most part, DoD program managers and engineers are working hard to achieve the objectives of the individual programs or activities they support. The buck doesn’t stop at the worker-bee. You know that but everyone seems to act as if the engineers don’t deserve their pay. It is probably management that deserves a cut in pay if they can’t get the engineers to do the right thing. Responsibility for slow program delivery has been and continues to be caused by poor management in DC, not just at OPNAV where until recently, nobody has seen fit to develop an integrated architecture, but also by Congress, when they tie up funding for absurd reasons and deliver funds only in spurts, making it near impossible to have consistency in contract support. Then, at the various activities, senior managers, many of whom come from the military and have no real experience in designing, building, integrating, or testing actual systems (hardware, software, or both), are too easily engaged with the latest buzz word and believe hype and magic. To make it worse, they want briefings, regularly, showing how a given program or effort is now aligned with the hype. For example, the hype about “data analytics” which so many thought would bring magic algorithms that would solve problems that still require good algorithms. Good people are working data analytics but it requires a good deal of analysis to make these tools work for our complex set of data and our fielding environment. Another example, the hype of model-based systems engineering. While true that these tools are available, proper use of them requires access to the right data on each system plus a solid understanding on the part of management and analysts of the limitations of the modeling system.
Thanks for the good feedback. I love it that this subject has created many good discussion comments and that it raises that passion in almost all of us that have worked in this area most of our lives. What we all know is that it must get better and it needs to start asap. Here is another good link to an Air Force DCGS Col. that is working on fast IT acquisition: http://www.popularmechanics.com/military/research/a24081/what-the-pentagon-can-learn-from-app-developers/
I have been talking about the stifling DoD bureaucracy since beginning this blog site but now it has been revealed by a study funded by the DoD that indeed the amount of bureaucracy really is excessive and measurable. Check out, Pentagon buries evidence of $125 billion in bureaucratic waste: http://www.msn.com/en-us/news/us/pentagon-buries-evidence-of-dollar125-billion-in-bureaucratic-waste/ar-AAlbC2l?li=BBnbfcL&ocid=iehp#image=2
Here is a good article on how DIUx is pushing for the use of Other Transaction Authority contracting. Good way to speed up the early prototype development and possibly buy commercial IT: https://gcn.com/articles/2016/12/06/diux-cso-ot.aspx?s=gcntech_071216
It’s not the lack of acquisition reform, firing government workers or putting hope in a single elected official. It’s basic culture of a system that by its very nature is not designed to deal with the cybersecurity threats we face. DoD has a core mission, it does that mission better than any other nation on Earth. What this group is trying to do is put a square peg in a round hole. I have the deepest respect for the author and a majority of those that provided feedback. At the end of the day, the Navy mission and culture will not, and frankly should not change to meet a threat that it is fundamentally not designed to win. If we really get down to it, we need an entirely new approach and are wasting money, time, and talent trying to meet a mission that is fundamentally not in the best interests of our nation to be served by the traditional model. We created the Air Force for a reason. We need to stop dividing up the resources amongst the current community and fundamentally reshape the DOD and our government to face what until now has been a nuisance, not a true global conflict. The US Navy does what it does better than anyone else. Make that priority one and leave cyberwarfare to a new organization with the right mission and focus. A cyberwar is at our doorstep. We need to appreciate that a kinetic force is essential, but that has not stopped or even slowed down our adversaries in this new battlefield.
Christopher, thanks for the thoughtful reply and good comments. Admiral (Ret) James Stavridis has made the case for several years that our Nation needs a new Military Service to address cyber warfare much like we formed the Air Force to address the new world of aviation warfare following WWII. I agree that such a Service may need to be formed to more effectively deal with what cyber warfare is all about, as you suggest. However on the matter of defensive cyber warfare every Service must be effective at preventing cyber warriors from preventing the kinetic effects they are designed to deliver, just as the Air Force could not eliminate the need for Army and Navy to maintain effective air defenses. The issue is how to go about that challenge.
I agree 100%. At the same time, without someone to steer that ship via a new org structure, I think the individual Services will struggle and we will not be optimized at the DoD level. That in and of itself presents a greater challenge and if done correctly could provide the leverage to enable the acquisition reform you so accurately capture in the article. Thank you for your insights and very valuable contribution to the issues at hand.
http://thehill.com/policy/cybersecurity/309489-senate-votes-to-elevate-cyber-command
Marv, thanks for sharing your insights and well reasoned solutions. Might you also consider commenting on the potential affects of maximizing commonality of deployed C4I systems within this context?
Returning acquisition oversight to Service level military control would indeed likely increase Speed to Capability, but should the Services also understand and then value their equity interest in acquiring integrated System-of-Systems capabilities vice procuring individual systems, components, and technologies quickly? My sense is continuing to empower Requirements Officers who appear to care first and foremost about their portfolio of individual systems, components and technologies is contributing to what we see today with our DDGs, that being almost each of the approximately 64 ships representing a unique collocation of systems, components and technologies that not only frustrates end-to-end testing of those systems and components prior to installation aboard ship, but frustrates operability, sustainability, and might also frustrate verifying cyber security and resiliency. While we’re eliminating the colors of money, might we also want to think about empowering and trusting those who should and would reallocate funding dedicated to specific systems to other components and systems in order to increase commonality of deployed C4I capabilities? One might suggest there’s considerable acquisition and operational value to having 8 well defined and tested DDG platform baselines with 8 DDGs allocated to each, vice 64 unique DDGs. What is a pound of commonality worth, and should it come at the expense of quickly deploying the best systems, components and technologies available? If commonality is a lower priority, then maybe SPAWAR ought to rethink its 2016 Strategic Objective 1.A: Increase Commonality of Deployed C4I Configurations.
Thanks in advance for your thoughts Marv.
w/r Joe
Marv,
We have an acquisition system that is designed to make sure that nothing ever goes wrong. Hence the “checkers” to Doers” ratio that is so out of proportion. As a result, everything that (eventually) gets done gets done VERY slowly and the technology is necessarily out of date by the time that platform or system is fielded. You have to be willing to accept some churn (and maybe even some bad decisions!) in order to get anything decent accomplished. By the way, I don’t see any words about the convergence of the IT and non-IT worlds. The non-IT folks will NEVER accept CIO authority (and shouldn’t, in my opinion) but many of the rules have been set up by CIO folks and might not work for non-IT worlds. How will be square this circle?
Thanks Troy, good comments. My comments may have been confusing but I am suggesting that IT and some embedded IT be managed under oversight of the Service and DoD CIOs reporting to their respective Cyber Commands, and that all other acquisition fall under a Senior Military Officer reporting to the Chief of Service Staff.