“In today’s globalized world… …this approach couldn’t be more ill conceived!”
The DoD currently attempts to mitigate cyber threats through onerous certification processes and drawn-out acquisition decision and implementation timelines. In today’s world plagued with cyber criminals and dedicated state sponsored cyber warriors, this approach couldn’t be more ill conceived!
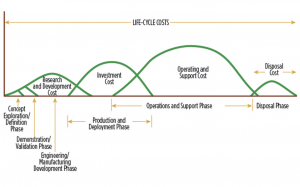
Like all of DoD’s acquisition and budgeting processes, programs of record are funded using some version of the spending curves shown on the right. These traditional spending curves align well with weapon systems that are researched, developed, purchased, sustained, and disposed, in the life-cycle phases shown. Each curve looks like a hill with funding going from small to large and then back to small, associated with the phased effort, purchased materiel and expenditures involved. This onerous practice may appropriately cover DoD platforms or weapons, but given the reality of modern commercially driven information technology (IT) and cyber vulnerabilities, it is radically misaligned with the DoD’s critical need for cybersecurity and IT capability.
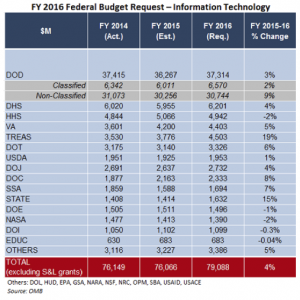 The chart on the left shows Federal IT budget requests from FY14-FY16. Looking across the columns, it is easy to see that dollar amounts remain relatively constant year-by-year. Yet inside of each of these department requests the IT programs of record are funded following the approved budget hills. To get those budget hills approved and funded, each department spends enormous time and energy working lengthy approval processes involving requirements stakeholders, department comptrollers, and eventually Congressional budget approval committees.
The chart on the left shows Federal IT budget requests from FY14-FY16. Looking across the columns, it is easy to see that dollar amounts remain relatively constant year-by-year. Yet inside of each of these department requests the IT programs of record are funded following the approved budget hills. To get those budget hills approved and funded, each department spends enormous time and energy working lengthy approval processes involving requirements stakeholders, department comptrollers, and eventually Congressional budget approval committees.
These budget hills are further compromised because approved funds are allocated into types of money, such as research & development, equipment purchase, and maintenance/sustainment. Each funding type can then only be used as designated leaving little to no flexibility for changing how funds are used during the execution year.
The often proclaimed purpose of this complicated budget activity is good stewardship of public tax-dollars. Most DoD contracting officers further work to drive down IT contract personnel costs and IT contract profit margins. The unintended consequences of these long standing practices are IT systems that are old and full of cyber vulnerabilities because of:
 unproductive human process churn;
unproductive human process churn;- ineffective use of IT funding;
- lowered IT contractor skill sets; and
- very long IT implementation and upgrade times.
For a deeper understanding of DoD contracting challenges, I recommend Daniel Goure’s report, Incentivizing a New Defense Industrial Base, shown to the right.
“…state-of-art IT products reduce cyber vulnerabilities…”
It is well understood within the commercial IT technology community that state-of-art IT products reduce cyber vulnerabilities, as explained in Cole Humphreys’ article, “The Risks And Hidden Dangers Of Outdated Technology.” The Federal/DoD catch 22 is that it is impossible to field state-of-art IT systems. So while the Office of Personnel Management struggles to dig out from under the massive SF86 personnel clearance data loss, and DoD continues to lose valuable military weapon system design data to cyber theft, nothing is being done to address slow IT acquisition and upgrades cycles which are the root cause of the problem.
“The Federal/DoD catch 22 is that it is impossible to field state-of-art IT systems.
The unrecognized reality is that DoD could remain at the leading edge of IT and cyber security within current IT budget levels. To understand how we need only review commercial company IT budget and implement practices. Within these companies, just as in the DoD, IT budgets are relatively level year-to-year. However commercial Chief Information Officers (CIOs) and Chief Information Security Officers (CISOs) execute yearly plans without artificial budget constraints on adding or reducing IT personnel, upgrading needed capability, mitigating cyber vulnerabilities, or retiring older systems. Because these CIOs/CISOs know budgets will remain relatively constant, they plan for upgrades and execute new opportunities within months and years, rather than the years and decades required within the DoD. Unlike the Federal government, commercial budgets are planned around level funding that varies only when new opportunities justify seed funding for significant upgrades. As is often the case in IT, upgrades can reduce the cost of operations & sustainment thereby creating a self-funding effect for the remainder of an upgrade. By continuing these efficient IT upgrade cycles, commercial IT companies are able to increase IT capability while reducing cyber vulnerabilities, all within nominal yearly funding levels.
Using the DoD’s current levels of IT funding, if commercial IT spending and upgrade practices were adopted, DoD IT capabilities would remain closer to state-of-art, thereby reducing cybersecurity vulnerabilities. Further, as IT capabilities are modernized, IT support to mission improves in a continuous cycle of upgrades and improvements.
To create this continuous improvement cycle DoD should:
- Plan for, and help Congress understand, that DoD IT budgets will always remain within a few percent of the previous year’s budget;
- Include within the IT budget, IT support and maintenance, cybersecurity operations support and maintenance, IT/cyber upgrades, and all IT personnel costs, to include contract support personnel;
- Allow IT/cyber budgets to be used flexibly to cover item 2, year-by-year;
- Eliminate the budget hills and colors of IT money, and concentrate yearly budget decisions around seed funding to improve IT and cybersecurity capabilities; and,
- Contract for best IT capability in the shortest amount of time without contracting to reduce contract margins and IT personnel costs.
Today, commercial companies are conducting proof of concept testing on state-of-art software defined data center (SDDC) technologies. These virtualization products are providing order of magnitude reductions in rack space & power, while reducing cyber vulnerabilities, increasing IT mission capabilities, and reducing personnel requirements through system setup and administration automation. If DoD were capable of quickly adopting SDDC technologies into existing IT systems, the same advantages would accrue across mission and business systems. Flexible IT upgrade cycles would then continue to reduce cyber vulnerabilities while improving DoD’s warfare capabilities year-by-year!

This is an additional argument for the adoption of open source software. You get source code, the latest updates easily accessible, faster code response from internal hacks or backdoors, and reduced costs.
Georges, open source software is another story that is much more complicated than just the arguments you are making. It would be a good topic to blog about so perhaps in a future conversation we can explore it more
Marv,
Your observations on the economics of acquisition relative to IT are correct. A telltale is this: an information system worth its investment will outlive any of the components in it.
There’s a technical aspect to this too — it’s not just acquisition economics.
A good information system (good meaning one that will be around long enough to outlast its components) will be well modularized. A well modularized information system can sustain component updates without those changes cascading through the system — nothing changes until it all changes.
There are two reasons for good modularity; life cycle maintainability is one of them. The other reason is interoperability.
This good modularity applies to security just like anything else and here we are dominated by duct tape, not reasonable thinking. The issue is SCOPE of security:
– link security of a single link gets you security ONLY over that link. In the civilian world, WiFi security is a good example. The object secured is a frame and the entire frame structure is discarded no later than the first router.
– layer 3 security, VPN, secures datagrams so it can last as long as the datagram structure itself lasts. Which is over the network fabric. But not within end systems — the scope does not extend there. Layer 4/5 security (TLS, SSL https) secures connections, but again, the scope of the security stops at the edge of the end systems’ operating systems. The data is unprotected by these measures within the computer.
– layer 6/7 protection, by contrast, secures the DATA, not the infrastructure. A signature attached to a piece of e-mail contains the authentication of that e-mail end-to-end. S/MIME e-mail is the most elegant example of end-to-end encryption but there are more and potentially as many as there are applications. If the e-mail, to use the example, application is conceived properly, the security remains intact 1) over the internet, 2) through the MTAs 3)through sending and receiving UAs, and 4) in storage. The security is only removed on composing or editing.
Infrastructure protection security is important, but it can never been of adequate scope to meet the data security requirement. We’ve been excellent at solving the wrong problem.
b
Thanks Rex, always thoughtful and informative comments.
Layer 8 and 9, I like that… good way to talk about money and politics. Notice that one can’t fix the IT cybersecurity from layers 8/9. We need to start with layer 1 and weave solutions up the stack…
I just was pointed to a great article that details the much larger Dod acquisition problem. Peter Greenwalt’s article Five Factors Plaguing Pentagon Procurement, hits the nail on the head…
Great article Marv. The tech refresh and acquisition cycles have different timespans and need to synch up for greater decision making agility. Smart security is built in vice bolted on.
Great post, Marv!
Bottom line seems to be: in order to protect layers 1 – 7 properly, Federal Government has to change they way they approach IT from a layer 8 and 9 perspective (i.e., Money and Politics).
This, more than anything, would be an area where Federal can learn from Commercial.
~John
Having reviewed dozens of studies into DOD’s flawed IT/Cyber acquisition strategies, the root causes have been laid to bare; a dysfunctional acquisition process, lack of accountability of companies who guide these failures (FFRDC/SETA), and complete disconnect from commercial best practices and innovations. DIA’s David Shedd hit the nail on the head last year during an INSA event, stating, “in my experience, bureaucracies will always favor failure over change, as that is what they are comfortable with”. I concur with McCains desire to hand over service specific programs to the services to manage and hold them accountable for failures. Components will have an opportunity to break away from the byzantine waterfall DoD5000, JCIDS and DODAF following Clinger Cohen Act approaches that favor embrace of commercial IT innovations.
Marv, you hit the nail on the head in the title of your post. Until the cyber vulnerabilities created by the current acquisition system are proven to be fatal to a ship, aircraft, Soldier, Sailor, Marine or Airman, nothing will change. Even then…