In the January 2014 Proceedings article, Time for a U.S. Cyber Force, Admiral James Stavridis, U.S. Navy (Retired) and David Weinstein argue for an independent branch of the armed services, dedicated to cyberspace.
 “Cyberspace, like airspace, constitutes a vital operational venue for the U.S. military. Accordingly, it warrants what the sea, air, and land each have—an independent branch of the armed services.”
“Cyberspace, like airspace, constitutes a vital operational venue for the U.S. military. Accordingly, it warrants what the sea, air, and land each have—an independent branch of the armed services.”
A 5th military service dedicated to warfare in the cyber domain represents thinking that is critically important as information technologies (IT) continue to reshape how our world functions. However, just as the U.S. Air Force could not eliminate the need for Navy platforms to defend against missile and aircraft delivered warheads, a cyber military service will not eliminate the need for the Army, Navy, Marine Corps, and Air Force to maintain operational effectiveness in the face of cyber strikes directed at stopping, disrupting, or confusing ground, sea, and air operations.
Unfortunately the overly bureaucratic processes currently impeding DoD IT system modernization and life-cycle support, are even more damaging to the task of thwarting high-pace, high-dynamic, high-technology cyber attackers. Although significant DoD effort is currently directed at the implementation and certification of information assurance (IA), the results have proven to be more about additional cost and implementation time than real-world IA effectiveness.
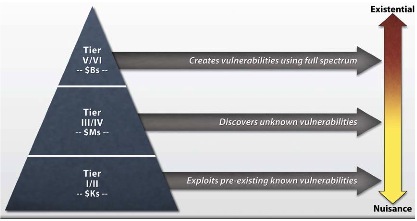
In January 2013, the Defense Science Board (DSB) issued a report on cyber security titled Cyber Security and Reliability in a Digital Cloud. This graphic, taken from the report, depicts a useful cyber threat taxonomy.
Using this taxonomy it is easy to understand that tier I and II amateur hackers, exploit known pre-existing vulnerabilities and do it on budgets in the thousand dollar range. Tier III and IV organized hackers discover and exploit unknown vulnerabilities supported by budgets in the millions of dollars. Tier V and VI nation state hackers create and exploit new vulnerabilities funded by budgets in the billions. If the U.S. is to sustain credible global military deterrence, it must effectively address the full dimension of these attackers twenty-four hours a day, seven day a week, and 365 days per year.
From my DoD experience I believe that the DoD Services and Agencies continue to embrace three primary IT myths that are pushing DoD IT systems and capability backward even as commercial companies and some public organizations are moving forward.
- The first myth is that DoD can not protect critical information if it is not managed and controlled within DoD’s physical base infrastructure.
- The second myth is that DoD IT must be directly administered and managed by it’s bulging 170,000 person IT government workforce augmented by additional contractor personnel.
- The third myth is that because DoD is special and IT system and applications require long acquisitions timelines, it is OK that most IT equipment is old and often no longer supported by the commercial suppliers.
These DoD myths would be warranted if the track record could be held up credibly against commercial organizations like Google, Amazon, Microsoft, IBM, Intel, and hundreds more. Because for commercial companies cyber vulnerabilities are the difference between being in business or not, these companies make it a top priority to reliably mitigate the cyber vulnerabilities of tiers I-VI. To do so they minimizing the human operators accessing their IT infrastructures and by remaining on the leading edge of technology and IA processes. Unfortunately within the DoD, minimizing IT system operators and remaining close to leading edge technology is not possible using current DoD IT processes and practices.
 By acknowledging and verifying this reality, DoD leaders could easily take advantage of commercial IT services for unclassified and low-sensitivity applications to achieve increased cyber security while saving human and budget resources. In turn, dollars saved on unclassified and low-sensitivity services could be invested into the classified systems to increased security and modernize IT systems that directly support front line military capability. DoD IT leaders could gain increased confidence in commercial IT service providers by understanding the FISMA (Federal Information Security Management Act 2002) certifications that have been granted to Google, Microsoft, Amazon, and others over the past two years.
By acknowledging and verifying this reality, DoD leaders could easily take advantage of commercial IT services for unclassified and low-sensitivity applications to achieve increased cyber security while saving human and budget resources. In turn, dollars saved on unclassified and low-sensitivity services could be invested into the classified systems to increased security and modernize IT systems that directly support front line military capability. DoD IT leaders could gain increased confidence in commercial IT service providers by understanding the FISMA (Federal Information Security Management Act 2002) certifications that have been granted to Google, Microsoft, Amazon, and others over the past two years.
Interestingly, the U.S. Intelligence Community through a newly awarded contract at the Central Intelligence Agency, is testing the ability of commercial IT services to provide secure, cost effective IT services to its classified users. This contract, provides IC physically protected locations where Amazon owns, installs, and operates Amazon Web Services (AWS) for IC users.  This bold move by the IC has promoted new thinking within the DoD. Several leaders in the military Service CIO shops and DISA (Defense Information Systems Agency) are investigating commercial IT service options. In addition to potentially providing modern IT infrastructure, these actions could help bring front and center the significant challenge of fielding tens of thousands of DoD legacy applications on modern IT infrastructure components; a good subject for a future blog post.
This bold move by the IC has promoted new thinking within the DoD. Several leaders in the military Service CIO shops and DISA (Defense Information Systems Agency) are investigating commercial IT service options. In addition to potentially providing modern IT infrastructure, these actions could help bring front and center the significant challenge of fielding tens of thousands of DoD legacy applications on modern IT infrastructure components; a good subject for a future blog post.
DoD’s top IT leadership post has recently turned over with the departure of DoD CIO, Ms. Terry Takai. The current Department of Navy’s CIO, Mr. Terry Halvorsen has been named as acting DoD CIO until a vetted, aproved replacement is named. With this leadership doorway open, all of us beneficiaries of U.S. National Security can only hope that with new leadership will come a rapid transformation toward efficient and effective DoD IT services, cyber security, and application modernization that will keep our young soldiers, sailors, marines, and airmen fully supported during the international challenges that lie ahead.
Independent of the potential for creating a U.S. Cyber Force as a fifth branch of military service, effective IT capabilities and unparalleled cyber defenses will be required if DoD is to remain a credible military deterrent. By beginning to recognize the three myths described above, DoD IT leaders could move much more quickly toward the adoption of leading edge commercial services as an important augmentation to the aging DoD IT infrastructure and legacy applications in use today.

Thanks Marv
Great insights as usual.
To take the arguement to the extreme, many DoD acquisition practices facilitate the ultimate insider threat; an institutionalization of Denial of Service. In the context of Cyber Warfare, they often create the functional equivalent of unilateral disarmament.
Dan
Great stuff Marv. We have been trying to get the DoD to at least look at Software Defined Networks (SDN’s) to rethink the way way the look at network security. SDN’s separate the data, and control plane’s. Of course we get the look of the RCA Victor dog with one ear up and a hunh every time we bring it up. Heaven forbid we introduce a new technology because some career IA person will certainly choke on that suggestion.
I noticed an agency used Amazon web services with a new product, or renamed product called vRouter from Brocade for the security solution. vRouter is a powerful virtual routing technology that can segment the virtual environment such as vmware’s ESXi.
It’s worth really looking at as we now run it in our labs.
Marv,
You know you’ll get no argument from me on this line of thinking. As the eternal optimist, I would like to think that the positioning of Sec Work into the DEPSECDEF job may help usher in a period of change for the next few years. If true, how to sustain the change will be our biggest issue as we slip into another cycle of political and military leadership changes.
Ron
Marv,
Great insight. The cloud is the future.
Joe
Network Insecurity
Copyright (C) 2014 Wilson F. Engel, III. All Rights Reserved.
Sometimes you are lucky enough to discover design without intending or planning to do so. For all the determinism built into networks and their security, network insecurity remains. The way we learn about our network’s vulnerabilities is through harmful effects of intelligent hacking.
A few years ago I was involved in discovering why all but two of our
Air Force network gateways were completely compromised and crashed in one of the most prolonged, concerted cyber attacks this nation has ever known.
At the time I worked at Hanscom Air Force Base, and I had tangential experience working with the Combat Information Transport System program, which was the program most affected by the cyber attacks. CITS is all the wired and wireless, land-based, airborne and via-satellite network infrastructure that the Air Force uses daily to communicate battle information worldwide. Its gateways are primary national assets.
When I was asked informally to investigate the attacks, I was coincidentally involved in another special project involving what was then called the Engineering Baseline. The purpose of that project was to discover software and hardware in our existing Air Force programs that could be re-used in other programs to reduce development and maintenance costs. This project was, it turned out, the perfect cover for investigating the cause of the successful network attacks.
In following the trail of discovery from my re-use program, I discovered that the only two gateways that had survived the attack had been among our foreign installations. Those two foreign gateways had been developed–each uniquely–by an old friend and fellow troublemaker in the Tactical Data Systems program, known for providing snap-on networks on demand worldwide. When you urgently need a network planted within days anywhere on earth with portable infrastructure for instant connectivity around the globe, you call the TDS program, and they provide it.
The development of those two gateways was accomplished without the knowledge of the CITS program management office and, particularly, the CITS configuration management team. The survivor gateways were rogue installations not sanctioned by the configuration management process at Hanscom. In other words, the vulnerabilities of those two gateways were unknowns from a configuration point of view. Those gateways were thus invulnerable to attacks in ways unknown to the program office.
The two rogue gateways were designed and integrated for maximum use of commercial off-the-shelf software by three genius-caliber technicians in a special project. The only rules for their development were that the each installation must work for the end users and that each must accomplish the CITS objective of continual, secure communication with 99% effectiveness. In the event of cyber attack, those two gateways accomplished their objectives when none of the other gateways accomplished them.
I learned in my investigation that at any given time an average of 273 critical un-patched vulnerabilities exist in the CITS gateways. Standard, approved processes and the unceasing production of hacks are guaranteed to keep this number constant. In other words, the configuration and security processes put in place by the CITS program to manage changes necessary to patch the gateways for known vulnerabilities lead inevitably to unacceptable outcomes for end users and the Air Force. As many new vulnerabilities are detected as are patched in a given time interval even though the network administrators work as hard as they can to accomplish their workload 24/7.
Unfortunately, the CITS program refused to adopt the lessons we learned from the success of the TDS program because those lessons were derived from rogue installations with insufficient documentation, differing engineering solutions, and lack of sanctioned configuration and security controls.
From all the above, I deduced three things:
First, the CITS program policies are major impediments to network security in the Air Force, but finding the right policies for networks will not be easy.
Second, rogue installations can be helpful in securing systems and networks, but their lessons must be incorporated in networks and gateways generally.
Third, and most important, the instigation of the successful attacks was most likely by insiders very knowledgeable about known, listed network vulnerabilities. In other words, Air Force uniformed or contractor personnel were likely involved somehow in the network attacks.
In designing networks for future use by the Air Force, I worked with the brainy CISCO offshoot f5 Solutions to evolve the “Sandwich Firewall,” which protects networks from both internal and external attacks. I and my teams also designed software that was called the Sentient Network. This artificial intelligence cyber defense software would recognize attacks instantly and remedy vulnerabilities automatically. This software is a Holy Grail.
I realize that no network will ever be impervious to all attacks and that every security measure is taken after a responsible weighing and acceptance of vulnerabilities. Just as it is impossible to install every security patch instantly, so it is impossible to guarantee the loyalty of underpaid, often frustrated, sometimes disgruntled network security personnel.
While I was investigating the attacks, quite coincidentally, I was asked by the Air Force to listen to a presentation given by representatives from a small Finnish company named Codenomicon. Stemming from an initiative at a Finnish university, this firm had a world-class operation with the best cyber command center configuration and user interface I have ever seen.
The company was working with the NSA and wanted to work with the Air Force. One of the key members of Codenomicon’s Board of Directors is the former cyber security chief of the White House. He and I are linked on Linkedin.
So go figure: what this nation cannot accomplish on shore, we (NSA and others) often must do off shore. This strategy can be beneficial, as in the case of networked, multiuse imagery solutions that were first developed in Singapore and Israel, then imported to the USA for use in our medical and intelligence communities.
Four vexing risks are associated with this offshore development approach:
(1) You have to do your development in full view of the global hacker community.
(2) You risk having the offshore capability used against you by other countries and non-nation-state actors.
(3) You cannot always devise a way to reposition capabilities built offshore back onshore where and when you need them.
(4) You risk losing the competitive advantage of your technical base by developing critical technologies off shore.
Note: In reviewing all the above with a brilliant young US Air Force officer and cyber warrior, the Major summarized the situation in one word– “Fundraiser!” His conclusion is that some Government contractor stood to make a lot of money devising the “fixes” for the damage that was caused by the attacks. The Air Force could ask for the money. Congress would appropriate it. You get the picture. On his opinion I have no comment.
Marv –
Thank you for the posting. Good ideas.
As you know ships must be able to operate in both connected and stand-alone modes, and in an unconnected mode must be able to have all information necessary for cyber protection and both local and wide network operation readily available.
The model must also work over limited bandwidth connections, and must be able to allow for secure remote monitoring and management assistance when needed.
With advanced technologies emerging, and the pressure for fewer personnel on a ship, autonomic and SCADA issues are also critical.
Also important is the ability to selectively share (RF) certain data with coalition forces with the understanding that the policies governing these connections may shift at any time.
With these issues in mind we support a blend of on-ship self-managed operation and protection with connections to a shore facility that can provide remote monitoring, management and operations. This could be through a commercial environment as you suggest.
Best
John Mullen
Great post, Marv – what about the ongoing myth that “DoD data is special”?
I believe that adversary targeting is greatly enabled by the myth of “special data” coupled with bureaucracy, arcane C&A processes, outdated risk mitigation/acceptance models, and acquisition processes that ensure only obsolete technology gets fielded. By the time anything actually gets fielded, and versions get locked in for xx years, and the attack vectors are already well known – this is only providing a false sense of security that really isn’t more than a house built on/of dust and sand.
As a result, DoD is significantly LESS secure than commercial organizations, despite the arrogant claims of having built a high walled garden of special protections around special data. It’s a true flaw of hubris, yet people continue to be surprised when things get compromised.
Marv,
Excellent piece! Thanks for the hyperlinks to the background information.
The DoD cannot do it alone – and commercial providers, properly selected, can aid and assist in this Cyber-fight, just as is done in wars on other fronts.
Thanks for giving us some insights to think about! We need help to join the effort!
Amy
The military’s “rush” to COTS to keep pace with technology and make systems less expensive has gotten us into the mess we are in now. The military needs to develop specific customized systems that meet their needs NOT with COTS. COTS systems apparently have no “real” requirement for security. Patch after patch after patch….
COTS motivation is profit, 1st to market, cheaper then the competition, more features (unsecure) then the competition, need i go on ? It is bad enough every single chip on the COTS systems are made out of this country and with little or any traceability or real supply chain security. Military specific systems with GOTS operating systems and applications for critical functions is what is needed or we will continue to chase our tail when it comes to securing systems. It may be more expensive but will be more secure.
Marv,
Great insight and overview!
The percentage of the DOD budget which is devoted to IT security is incredible especially considering the results they have gotten. Let’s hope Ms. Takai’s departure does not cause further delays in the IT modernization effort.
Commercial companies do not always “make it a top priority to reliably mitigate the cyber vulnerabilities of tiers I-VI.” Witness Target and their brethren. Because commercial companies and DoD use similar technologies (albeit DoD’s may be from an earlier generation), the attack vectors are similar. I agree that current practices prevent DoD from “remaining close to leading edge technology,” but that is an issue that overlaps only partially with vulnerability. Leading edge technology likely has zero-day vulnerabilities. Irrespective of the technologies, people may provide the vulnerabilities. Consider the successful Chinese whaling against commercial companies with presumably up-to-date technology.
Mar,
Excellent article, Marv. Commercial cloud based systems offer cost savings as well as clear advantages for cyber-security. Those costs continue to fall dramatically over time.
The DoD processes developed for fielding conventional weapon systems are less effective in the cyber domain. In addition to cyber protection, bureaucratic processes impede the agility DoD needs to rapidly field new cyberwarfare capabilities to exploit emergent adversary vulnerabilities.
Marv – Great insights as always! In my simplistic view, DoD needs to take a page from the the Navy’s playbooks that designed and built are most significant engineering achievements in the last century – nuclear power and AEGIS. You find the best mind in the business (i.e. Rickover/Meyer) and give them the authority AND funding to design and build the capability we need going forward. And one last step – they need to remove the barriers that result in our systems being outdated before they’re ever fielded!
Ken
Marv,
This is on the money. Could you expand the idea of “learning the lessons from Commercial organizations” to the concept of a Services-oriented architecture? The provision of services by one organization to the entire Navy has some real implications of acquisition models, development plans and maintenance of authoritative data/services.
Thanks! Curt